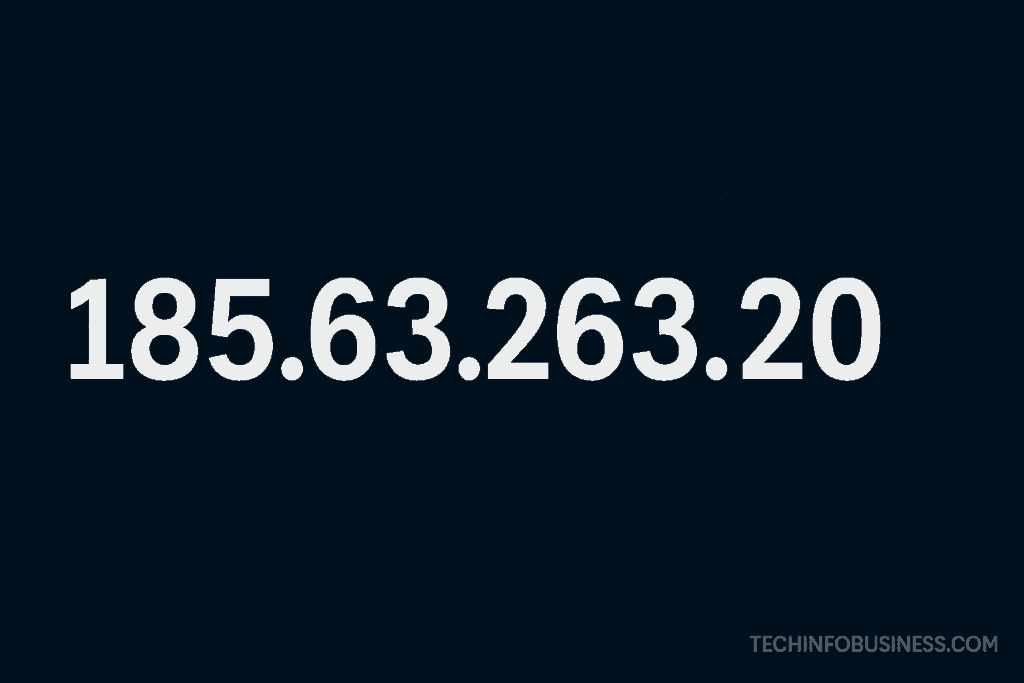In the vast and complex world of computer networking, IP addresses are essential elements that allow devices to communicate across the internet or local networks. While many IP addresses serve legitimate and critical functions, some stand out as questionable or anomalous. One such address is 185.63.263.20. At first glance, it seems like a regular IPv4 address, but upon closer inspection, it challenges the rules of conventional IP addressing and raises many important questions. This article aims to explore the structure, origin, validity, geolocation potential, and implications of this IP address in detail.
Understanding the Basics of IP Addresses
An Internet Protocol (IP) address is a numerical identifier assigned to each device connected to a computer network that uses the Internet Protocol for communication. The most widely used IP addressing scheme today is IPv4, which consists of four decimal numbers ranging from 0 to 255, separated by dots — such as 192.168.0.1.
Each section (known as an octet) represents 8 bits of the 32-bit address. IP addresses play a vital role in both identifying and locating a device on a network. The Internet Assigned Numbers Authority (IANA) and regional internet registries (RIRs) are responsible for assigning these addresses to organizations and internet service providers (ISPs) across the globe.
Why 185.63.263.20 Is Technically Invalid
Although 185.63.263.20 resembles a valid IPv4 address, it violates one critical rule of IP addressing: no octet can exceed the value of 255. In this case, the third octet, 263, is out of the permissible range. Therefore, 185.63.263.20 is not a valid IP address.
This discovery brings into question why this address might appear in network traffic logs or be flagged by cybersecurity tools. Invalid IP addresses can still be seen in raw logs, often as a result of:
- Typos or misconfigured software
- Deliberate obfuscation by malicious actors
- Testing and probing of network defenses
Such invalid addresses, though technically unusable, can reveal a lot about the digital landscape and the behavior of both legitimate users and malicious agents.
Common Reasons for Seeing Invalid IPs Like 185.63.263.20
When a system administrator or security analyst sees an invalid IP like 185.63.263.20 in logs, it can stem from several underlying causes:
1. Human Error
Misconfigurations or typos during manual data entry can easily result in IP addresses exceeding the allowed range. If an engineer incorrectly types an octet as 263 instead of 236, this kind of anomaly could arise.
2. Buggy Software
Programs that parse or generate IP addresses may have flaws. These bugs might fail to validate the values of octets correctly, resulting in malformed addresses.
3. Malware or Obfuscation
Malware creators and hackers often use invalid or spoofed IPs as decoys. By generating traffic using an invalid IP, they can attempt to confuse security systems, avoid IP-based blocks, or test detection capabilities.
4. Log Tampering
Attackers might deliberately inject invalid IP addresses into logs to throw off incident response teams or to create ambiguity during forensic analysis.
Cybersecurity Implications of 185.63.263.20
Though it is not a usable IP address, 185.63.263.20 might show up during cybersecurity investigations, particularly in honeypots, intrusion detection systems (IDS), and SIEM logs. Its presence can serve as a red flag. Here’s why:
- Reconnaissance Attempts: Some bots and scanners probe networks using invalid IPs to test firewall responses or the behavior of anomaly detection systems.
- Evasion Techniques: By injecting bogus addresses, attackers can mislead logging systems and security analysts, causing wasted time and inaccurate threat assessments.
- Log Pollution: Repeated appearances of malformed IP addresses can pollute logs, reducing their clarity and utility, especially in large-scale networks with millions of daily events.
For these reasons, security professionals need to remain alert and investigate the circumstances surrounding such anomalies.
Can You Geolocate 185.63.263.20?
Geolocation of IP addresses is a common method used to determine the approximate physical location of a device. Normally, services like MaxMind, IP2Location, and others can provide:
- Country
- Region
- City
- ISP or Hosting Provider
- Organization name
However, for an invalid address like 185.63.263.20, geolocation databases will not return any meaningful data. Since the IP is invalid, it doesn’t exist in routing tables and isn’t assigned to any ISP or country. Attempting to geolocate it will result in either a failed query or a placeholder response indicating “unknown.”
How to Investigate Malformed IPs in Your Network Logs
If you encounter 185.63.263.20 or similar malformed IPs in your logs, here is a step-by-step approach to investigate them:
- Check Log Context: See which service or endpoint the IP attempted to access. Was it during a login attempt, an API call, or a ping?
- Search for Patterns: Look for other anomalies in the same log entry — unusual request headers, payloads, or user agents.
- Validate with Tools: Use IP validation tools (like
ipaddressmodule in Python or online regex validators) to confirm whether the IP is structurally valid. - Use Threat Intelligence Platforms (TIPs): Search your threat intel database to see if similar anomalies have occurred elsewhere.
- Block or Monitor: If multiple malformed IPs are detected from a source, consider blocking the subnet (if valid) or flagging for ongoing monitoring.
The Importance of Validating IP Inputs in Development
From a developer’s perspective, always validating inputs — especially IP addresses — is a crucial best practice. If applications log or process invalid IPs without error handling, it can lead to a number of issues, such as:
- Incorrect Analytics Reports
- Faulty Access Control Decisions
- Misleading Logs
- Openings for Exploits and Attacks
In web apps, APIs, or server logs, always sanitize and validate IP input with appropriate functions. Many programming languages provide libraries for this, such as:
inet_aton()in Cipaddressmodule in Pythonfilter_var()in PHP
When Invalid IPs Are Used for Testing or Research
Interestingly, not all appearances of invalid IPs like 185.63.263.20 are malicious or accidental. Some researchers, cybersecurity professionals, or developers may use them intentionally for:
- Testing Error Handling in Software
- Simulating Malformed Network Traffic
- Penetration Testing Exercises
- Training Machine Learning Models on Anomalies
In such cases, the IP’s invalid nature actually serves a useful function: it introduces controlled errors into systems to test resilience and behavior.
Should You Block Invalid IPs Like 185.63.263.20?
Since 185.63.263.20 cannot be used for genuine communication, blocking it at the firewall level is generally unnecessary. However, here are considerations:
- Log Anomalies: Configure your IDS or SIEM to alert when malformed IPs are logged.
- Rate Limiting: Implement rate-limiting rules that apply even to malformed requests.
- Update Detection Rules: Include known invalid IPs or suspicious patterns in detection rules for added protection.
- Custom Alert Policies: Set up alerts for malformed IPs as potential indicators of reconnaissance or evasion attempts.
Ultimately, your security posture should focus on context and behavior rather than single events.
Read More: Uncovering Foxfiny com: Honest Review, Complaints & Shopping Tips
Final Thoughts on 185.63.263.20
The IP address 185.63.263.20 is a fascinating example of how something seemingly trivial — a malformed IP — can uncover deeper stories about system behavior, software design, cybersecurity, and even malicious tactics. Although invalid, its presence in digital environments shouldn’t be dismissed. From a forensic perspective, these anomalies can reveal configuration flaws, attack strategies, or overlooked bugs.
By combining careful analysis, input validation, and proactive monitoring, IT professionals can ensure that such anomalies are identified and understood — rather than ignored or misunderstood. As always in cybersecurity, the devil is in the details, and even a single digit can make all the difference.